This is not surprising because hackers often use “keylogers” to log all keystrokes of a user. Their aim is to intercept passwords, keywords and other important information. However, spyware can be very helpful sometimes. And there are examples and examples. For instance, a system administrator can install a spy on the local network server and he will always know if the computer was used or not and what operations were performed.
Of course, spyware has a wider range of purposes. Parents can use it secretly to see what children do with the computer when the parents are away. School teachers can use spyware to control their students’ activities. But it is especially useful when it is a part of the information security system on your computer. Yes, exactly, utilities usually used by hackers can help you resist them. To do it, the owner of the computer or its constant user should install this utility. After that, he or she will know who uses the computer and for what purpose.
However, it should be mentioned that it is not all spyware that can be used as a security tool. Such program must have a set of features that most keylogers lack. Let’s take Actual Keylogger developed by the Actual Keylogger Software company for example. This keyloger was developed as an aid to computer owners and their constant users.
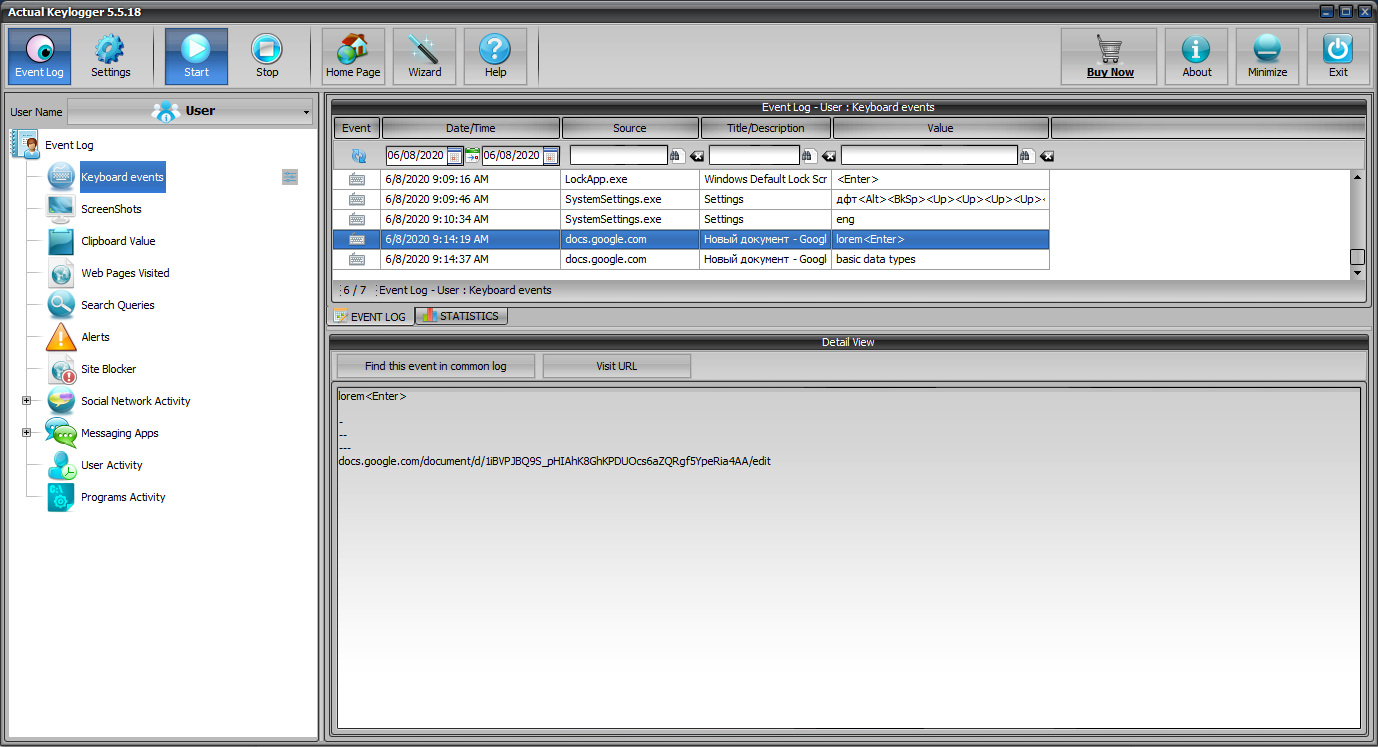
To start with, let’s name the main features of Actual Keylogger. The first one is “Keyboard”. As you can judge from its name, this module is responsible for logging all keystrokes. The utility also logs the case of each character and can easily log almost all key combinations.
Another pleasant thing is that Actual Keylogger does not log all keystrokes together, but groups them according to their programs. In other words, log files show the title of the window the text was typed in. At the same time, a lot of keylogers lack this feature and the PC owner cannot use the log files to tell what program was used to type the text. However, this information is very important because some keystrokes are quite acceptable in one program, but can be harmful in another. But that is not all. Another useful feature in Actual Keylogger is the “Show only characters” option. You can enable it using the corresponding checkbox in the log view window. After that, only the typed characters are shown instead of all pressed keys. It means actually that the user will see only the text typed while he or she was away. This feature allows you to make backup copies of your texts with Actual Keylogger. Suppose you are working in some program and it is suddenly closed because of a failure. The typed text will be saved in the log files of our keyloger.
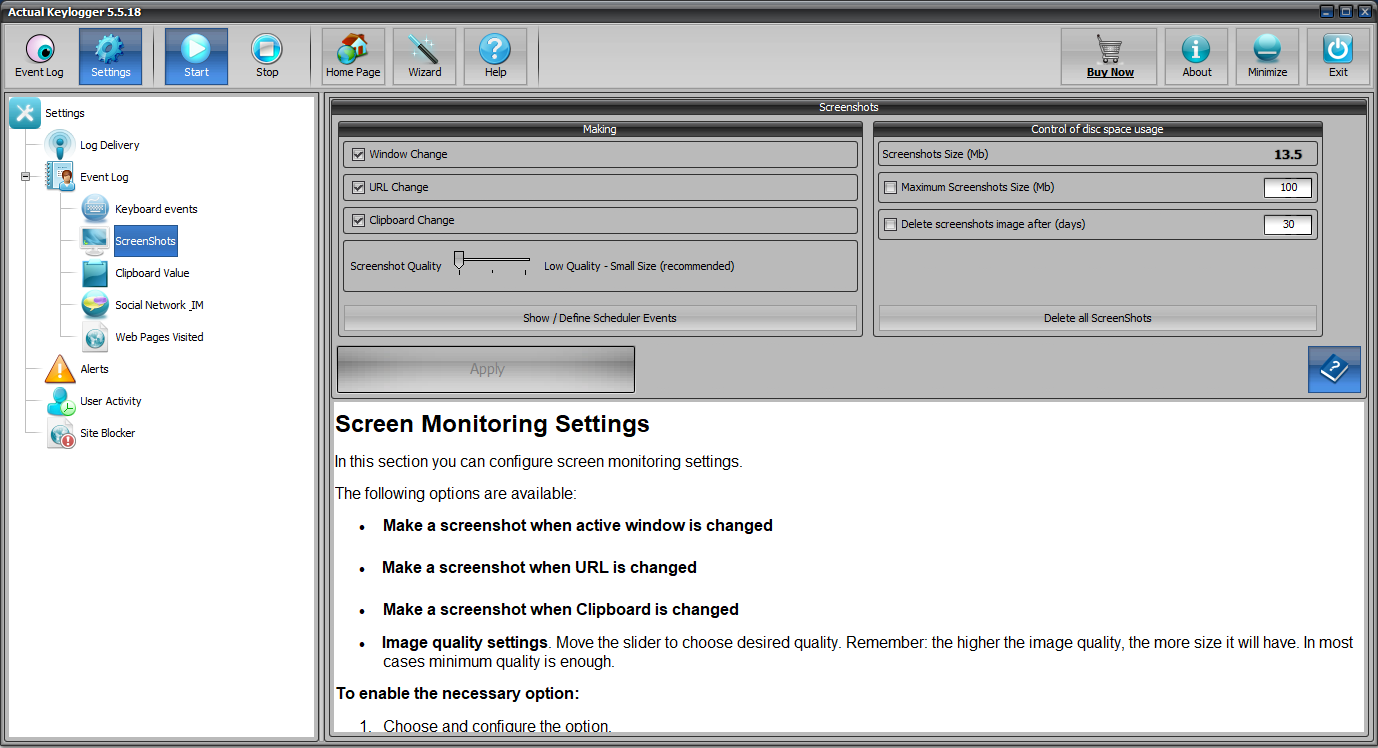
The next feature in Actual Keylogger is “Screenshots”. The program takes screenshots at the intervals the user specifies (by default – every 5 minutes). Now PC owner will see with his or her own eyes what the computer is used for while he or she is away. You can customize this option of course: specify the maximum space screenshots can take, their quality, hide the cursor from the screenshot, etc.
We move on to the next tab of the main window labeled “Programs”. It shows the list of software started and closed while Actual Keylogger was working. And actually they are not programs, but windows.
And, finally, here comes the last tab in Actual Keylogger labeled “Clipboard”. Everything is also quite obvious here. It shows everything that was copied into the clipboard during the work of the spy. Most users will not find this feature interesting, but it can be very useful sometimes. The clipboard is often used to copy long and complicated passwords. So if you see a keyword in the clipboard list, you know that you should change it as soon as possible.
So, we have examined the main features of Actual Keylogger. Now let’s talk about the special features of this spy. First, Actual Keylogger is an invisible program. You will not see any signs of its presence in the system and antivirus programs will not detect it. Moreover, in the program settings you can select such options as “Remove the shortcut from the desktop”, “Remove the program from the menu”, “Remove the program from the “Add or Remove Programs” list” and “Hide the program folder”. If the PC owner enables these options, nobody will even suspect that there is spyware on the computer.
Besides, it is really great that Actual Keylogger can protect its log files from unauthorized access. The PC owner can install a password that must be entered every time Actual Keylogger is started. Besides, all data the program saves is automatically encrypted. Thus, it is hardly possible to read the log files without using the Actual Keylogger utility.
And the last part of our review will be devoted to reports. Actual Keylogger can generate reports based on its log files in two formats: text or HTML. The user can specify the necessary time interval and select necessary types of log files. But there is more to it than that. Actual Keylogger can also create reports automatically and send them to the specified e-mail address. Moreover, the reports can be generated either at the specified intervals or when the log file exceeds the specified size (both parameters are specified by the user). A lot of system administrators will appreciate this feature because they will be able to immediately respond to someone's work on the server.
So we can see that the advanced Actual Keylogger can be an important part of the information security system. This utility will be really helpful to both the system administrators of local area networks and home users.
